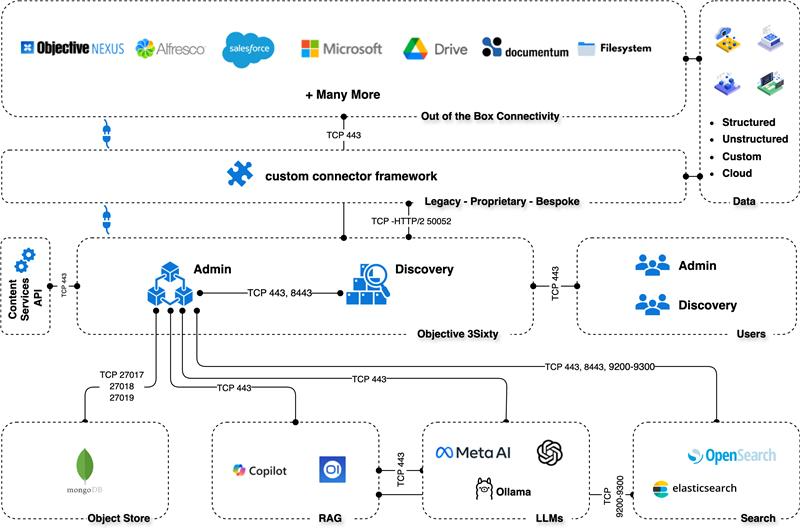
3Sixty Architecture
3Sixty Components
-
3Sixty Admin
-
Discovery
-
MongoDB
Network and Firewall Requirements
3Sixty Admin
-
Listen (TCP) Ports 80 and/or 443
-
Communicates with MongoDB on (TCP) ports 27017, 27018, & 27019
-
Communicates with Discovery on (TCP) port(s) 443 and/or 8443
-
Optional: Communicates with Active Directory on ports: (TCP, UDP) 445, (TCP, UDP) 88, (UDP) 389, (TCP, UDP) 53
-
Optional: Communicates with LDAP on (TCP) 389, (TCP) 636
Note: Communicates with CMIS and/or ECM platforms using vendor documented ports and procedures.
Discovery
-
Listen TCP Ports 443 and/or 8443
-
Communicates with 3Sixty Admin on (TCP) ports 80/443
MongoDB
-
Listen Ports 27017, 27018, & 27019
Certificates
3Sixty Admin & Discovery:
-
Please refer to the following link Tomcat SSL for documentation of how to generate and enable SSL certificates.
Access & Permissions
3Sixty Admin & Discovery:
-
Windows Local or Domain user with Read/Write permissions to Install and Tomcat Temp directory
-
Linux Local or LDAP user with Read/Write permissions to Install and Tomcat Temp directory
Passwords and Encryption
Database Password
-
In the simflofy-global.properties file there is an option to encrypt the database password: simflofy.encrypt.db.passwords=false
-
Setting this to true will encrypt passwords using 3Sixty's default encryption.
Connector Passwords
-
All fields marked as passwords in the 3Sixty UI are encrypted in the database and never returned to the User Interface.
Encryption Strength
-
By default, 3Sixty will use whatever the default encryption strength is for Java. If you wish to use the more secure AES 256, you will need to do 2 things:
-
In the simflofy-global.properties file, set this setting: simflofy.aes256.encryption=true
-
Install the JCEK policy file. JCE Unlimited Strength Jurisdiction Policy Files 7 Download
-
For 256 you need the unlimited Strength Jurisdiction Policy file below. In some countries you will not be able to use this file. AES-256 Encryption with Java and JCEKS
Related Articles: